Scenario:
R. Phoenix was hired by a startup company called Secure4Sure to see if he can circumvent their existing security policies in place in preparation for a 3rd party audit. Before the engagement, both parties were aware of the limitations of the security assessment. R. Phoenix agreed and signed documents, such as a Rule of Engagement (RoE) and a Non-Disclosure Agreement (NDA) document so everything is official and within boundaries.
On the first day, R. Phoenix used his social engineering skills and pretended to be an applicant for a network engineer position posted by the company on a famous job searching website. He handed over his fake ID and resume to the front desk personnel, and was immediately granted a day pass. Off he went to the office of the Senior Network guy for an interview. R. Phoenix immediately noticed the abundance of network cables lying around connected to the wall’s Ethernet port. Old network devices and other gadgets are present as well.
Noticing the lack of a water fountain on the area, R. Phoenix asked the Senior Network guy for a glass of water. The guy politely nodded, asked him to take a seat and went out of the room to get a glass of water. R. Phoenix quickly grabbed a tiny USB device tucked on his left shoe and immediately plugged it in on one of the wall Ethernet ports. He created a small program that automatically sniffs the traffic of an IP network and dumps the result as a text file on his tiny USB drive. It only took him 15 seconds to sniff the IP network; thanks to an unsecured wall Ethernet port.
R. Phoenix went over with the interview and the entire process. Shook hands with the interviewer, surrendered his guest day pass at the front desk, and went straight home. He immediately booted up his computer, launched his favorite packet sniffer program and started to conduct network analysis. He was smiling while scrolling around the packet capture because on his first day, he already has all the information he needed along with a solid plan on how to penetrate Secure4Sure’s network.
He simply saw a multicast traffic to 224.0.02 and he knew what to do next. "The menu for tomorrow is either Denial of Service (DoS) or a possible Man-in-the-Middle (MiTM) attack baby!" he said to himself.
And the rest of the events that unfolded are history.
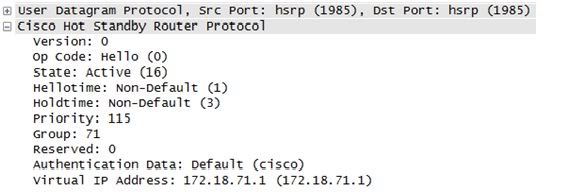
HSRP multicast

No authentication enabled, default password (cisco)
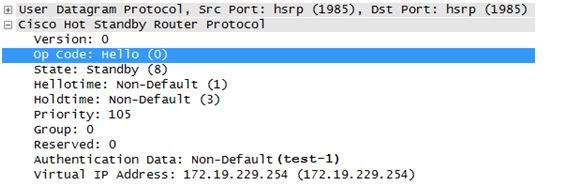
Weak authentication in HSRP, non-default, plain-text password (test-1)
Lessons Learned:
This attack is nothing new. A clever social engineer can easily bypass all your policies and technical controls in place. If someone wants to gain access to your network given enough means, motive, and opportunities (MOM) they will gain access. A bonus to them is lousy configuration on a network device.
What happened with the scenario above is simple; they want high availability on their IP network and they implemented Cisco's HSRP without an acceptable authentication in place. Without an acceptable authentication in place, a rogue router can be inserted in the network to participate in exchange of HSRP traffic (MiTM). This router will be configured with the highest priority so it acts as the primary router in the HSRP network. Then all traffic can be sniffed from this rogue router that the bad guy has complete control.
Because their network traffic was sniffed, an HSRP packet was discovered containing no acceptable authenticaion in place. A bad guy can also forge packets to mess with the HSRP multicast packets; inducing a DoS attack to the network.
Using plain-text passwords for HSRP authentication will suffer the same fate. The solution is to use the command to enable MD5, so the password is hashed and not transmitted as plain text over the network. Hashing provides the elements of confidentiality and integrity.
An Ethernet port without a MAC-based authentication in place is another door of opportunity. The best thing to do is to shut down ports not in use.
Links below will help:
Hijacking HSRP
http://packetlife.net/blog/2008/oct/27/hijacking-hsrp/
RFC 2281
http://www.ietf.org/rfc/rfc2281.txt
Cisco HSRP
http://www.cisco.com/en/US/tech/tk648/tk362/tk321/tsd_technology_support_sub-protocol_home.html
Cisco HSRP MD5 Authentication
http://www.cisco.com/en/US/docs/ios/12_3t/12_3t2/feature/guide/gthsrpau.html
Man-in-the-middle Attack (MITM)
http://en.wikipedia.org/wiki/Man-in-the-middle_attack
Scapy
http://www.secdev.org/projects/scapy/
Means, motive and opportunity (US Criminal Law)
http://en.wikipedia.org/wiki/Means,_motive,_and_opportunity
Hope this helps, shout outs to the guys at Pauldotcom.com, the best security podcast in the planet!
Ron(guerilla7)
http://packetboyperseus.blogspot.com